Open a micro letter and sweep a two-dimensional code
Subscribe to our WeChat public number
Turn on the phone and sweep the two-dimensional code
You can access the website and share it with your friends through a mobile phone

The State Council, China’s cabinet, promulgated an Administration Regulation on Cyber-data Security (the “Cyber-data Security Regulation”) on September 24, 2024. The Cyber-data Security Regulation, which will come into force on January 1, 2025, aims to implement China’s Cybersecurity Law (“Cybersecurity Law”), Data Security Law (“DSL”) and Personal Information Protection Law (“PIPL”) by interpreting principles outlined in these laws and detailing responsibilities and obligations that companies and individuals will shoulder when processing cyber-data and personal information.
1. Applicability of the Cyber-data Security Regulation
Cyber-data Security Regulation applies to cyber-data and personal information processing activities by cyber-data processors within China, and in some cases, outside China:
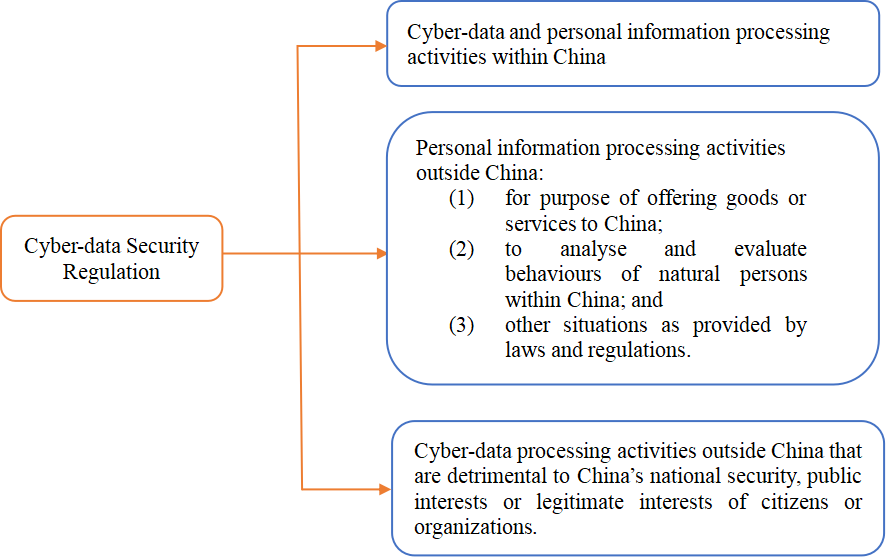
In the Cyber-data Security Regulation:
“cyber-data”refers to any electronic data processed and generated through network;
accordingly, “cyber-data processing activities”include collection, storage, use, processing, transmission, provision, disclosure, deletion and other handling of cyber-data;
a “cyber-data processor”, similar to a personal information processor under the PIPL, refers to an organization or individual who discretionarily determines the purposes and means of processing in the cyber-data processing activities. To further regulate processing activities of internet platform operators in their operations, the Cyber-data Security Regulation introduces “internet platforms” and “large-scale internet platform”, in which “large-scale internet platform” specifically refers to an internet platform who has more than fifty million registered users or more than ten million monthly active users, and operates complicated types of businesses and cyber-data processing activities which have important impact on national security, economic performance, national welfare and the people’s livelihood.The Cyber-data Security Regulation will not apply to any personal information processing by a natural person for his/her personal or family matters.
2. General Requirements of the Cyber-data Protection
2.1 Cyber-data processors will be required to adopt more detailed data protection measures
The Cyber-data Security Regulation details various obligations in respect of data protection that cyber-data processors should perform under the DSL.
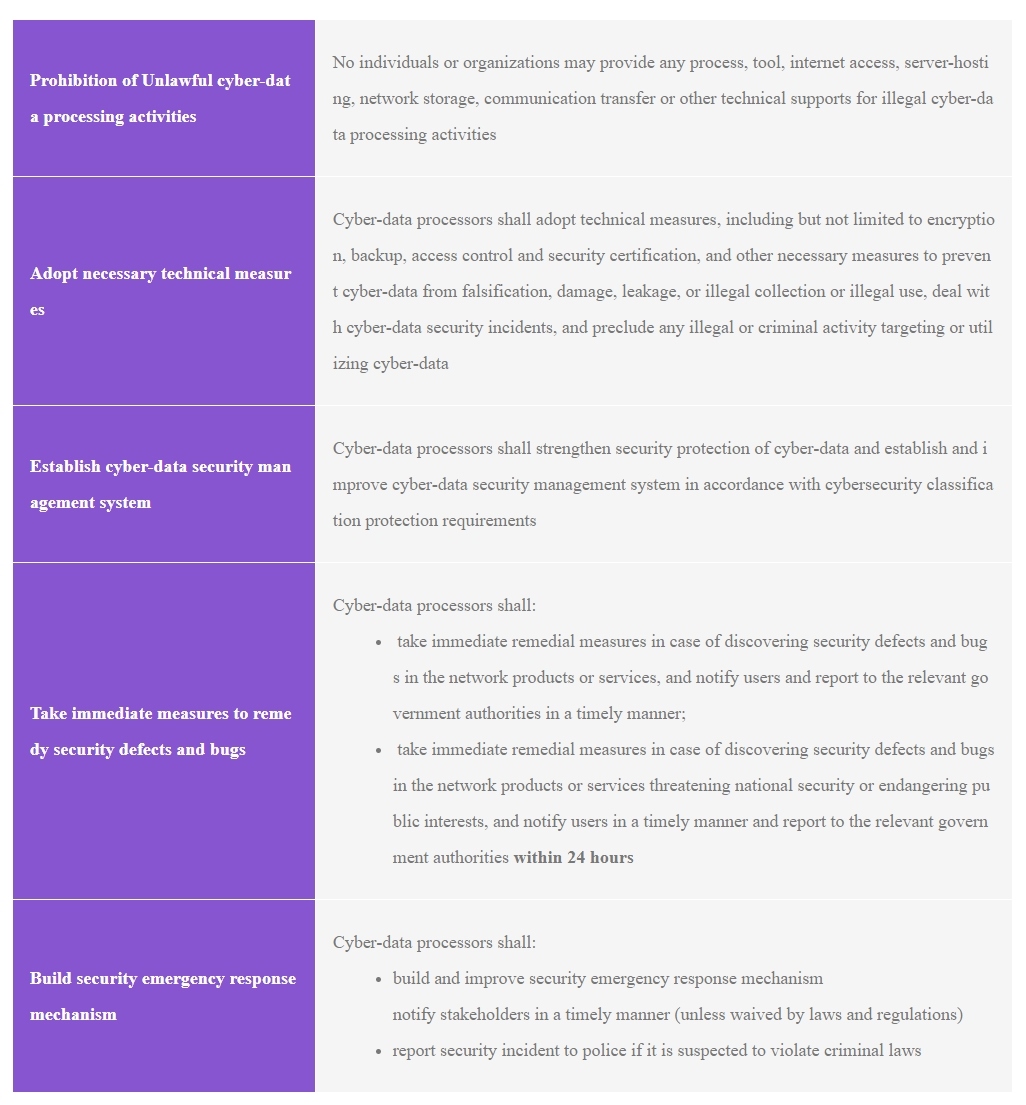
2.2 Cybersecurity review
To maintain consistency in the regulatory processes stipulated in the Cybersecurity Law and DSL, the Cyber-data Security Regulation requires cyber-data processing activities which affect or may affect national security to go through cybersecurity review in accordance with the Cybersecurity Review Measures effective February 15, 2022.
3. Special Protections to Important Data
The DSL declares to establish a data classification and hierarchical protection system. It has broadly classified protected data as core data, important data, and other data. It further provides that important data will be defined by general and specific catalogues, and further obligations are set for processing of important data. Core data carries that greatest importance and will have a tighter system of management.
3.1 What is important data?
Under the Cyber-data Security Regulation, “important data” refers to data in specific fields, specific groups, specific regions, or data that reaches a certain accuracy and scale, which once falsified, destroyed, leaked, or illegally collected or used, may directly endanger national security, economic operations, social stability, public health and safety.
3.2 How to share, subprocess and co-process important data?
Subprocessing, as defined by the Cyber-data Security Regulation, refers to cyber-data processing activities that cyber-data processor entrusts individuals or organizations to carry out in accordance with the agreed purposes and methods, while co-processing refers to cyber-data processing activities in which two or more cyber-data processors jointly decide on the processing purposes and methods of cyber-data.
The Cyber-data Security Regulation underscores the requirements of data security and retention records in terms of sharing, subprocessing and co-processing important data. Specifically:

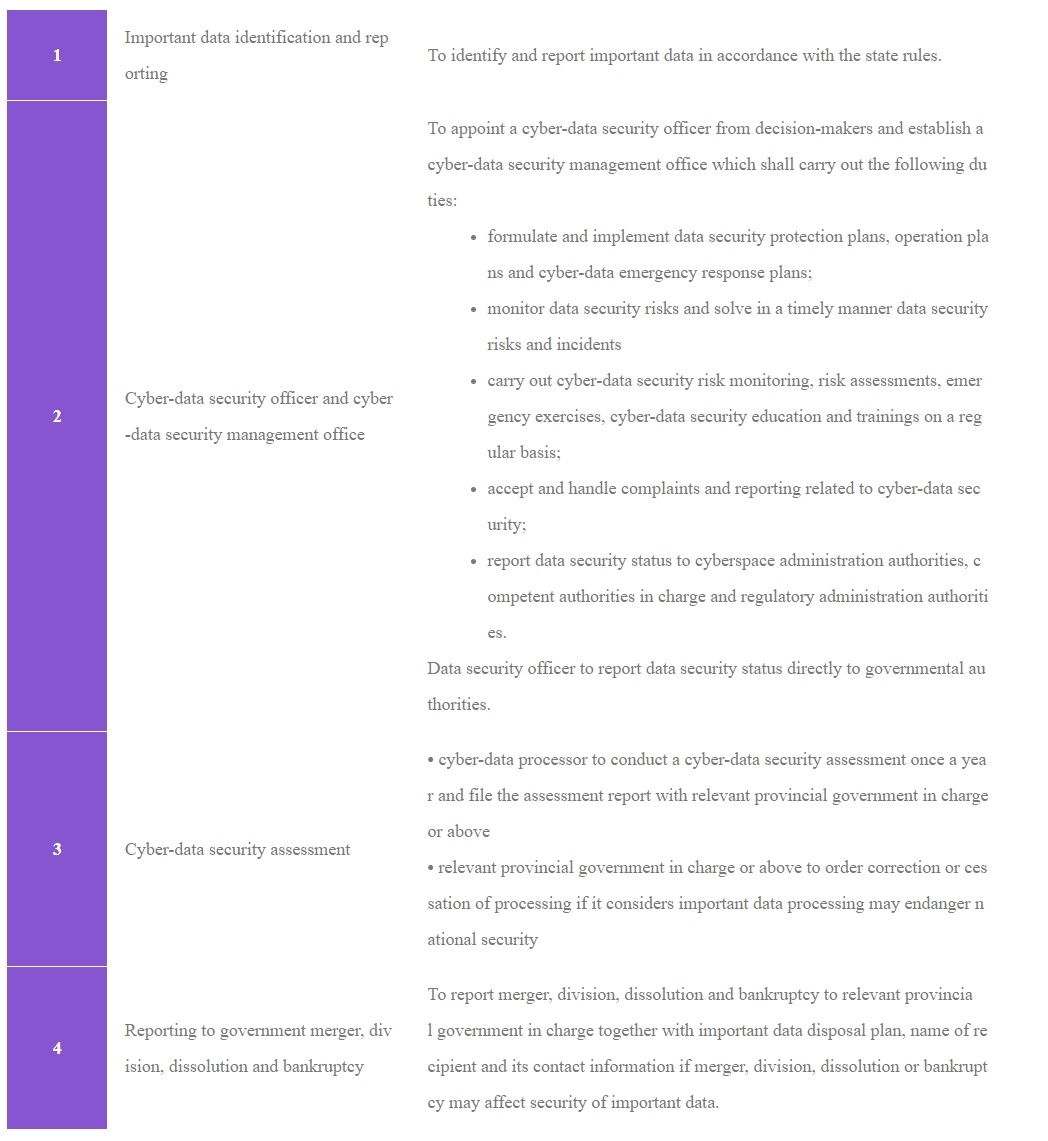
3.3 Other special protections to important data
Cyber-data processors must perform the following special security protection obligations to protect important data:
4. Cross-border Cyber-data Transmission
4.1 Legal bases of cross-border data transmission and exceptions
The Cyber-data Security Regulation allows cyber-data processors to cross-border transmit personal information under any of the following situations:
where it has passed prior security assessment organized by CAC; or
where it has completed personal information protection certification by qualified professional institutions; or
where it has entered into a contract, based on the standard contract clause enacted by CAC, with overseas recipient; or
where it is necessary to provide personal information to overseas entities in order to enter into or perform contracts to which individuals are one of the parties; or
where it is necessary to provide personal information of employees to overseas entities when implementing cross-border human resources management in accordance with labor regulations and collective contracts signed in accordance with the law; or
where personal information must be provided to overseas entities in order to perform statutory duties or obligations; or
where personal information must be provided to overseas entities in order to protect the life, health, and property safety of natural persons in emergency situations; or
other conditions as required by the applicable laws and regulations or CAC.
4.2 Security assessment of cross-border important data transmission
Where cyber-data processors transmit important data abroad, they must pass the prior security assessment organized by CAC. The Cyber-data Security Regulation further clarifies that as long as any data does not fall into any category of important data informed or public announced by the relevant region or government authorities, cyber-data processors are not required to go through CAC-led security assessment for important data.
4.3 Other general obligations in terms of cross-border data transmission
Cyber-data processors shall not transmit personal information or important data abroad beyond the purposes, means, scopes, types and scales of the cross-border transmission as stated as approved by the CAC-led security assessment.
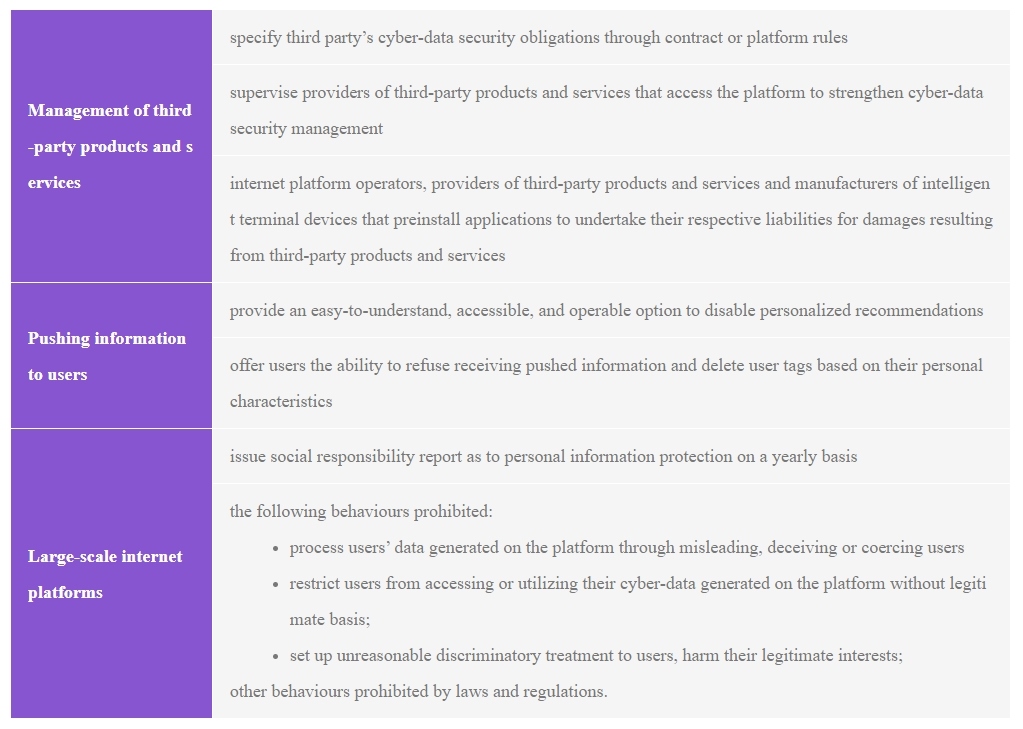
5. Closer Scrutiny Requirements of Internet Platforms
The PIPL has imposed special obligations on internet platforms who provide important platform services, have huge quantity of users and operate complex business types. However, it fails to define what such internet platforms really mean. The Cyber-data Security Regulation introduces internet platforms and large-scale internet platforms and underscored heavy obligations to be performed by their operators. For clarity, the Cyber-data Security Regulation defines “large scale internet platform” as a platform with over 50 million registered users or more than 10 million monthly active users, with complex business types whose network data processing activity significantly impacts national security, economic operations, or public welfare.
6. Personal Information Protection
6.1 Detailed requirements on personal information processing rules
The PIPL provides high-level requirements on personal information processing rules: (1) personal information processing rules must be made public for easy enquiry and retention; (2) processing personal information of the minors under the age of 14 must have special processing rules; (3) individuals have the right to request personal information processor to explain its personal information processing rules.
The Cyber-data Security Regulation clarifies the above-mentioned high-level requirements as follows:
(1) personal information processing rules must be publicly displayed, easy to access and put in a noticeable place;
(2) personal information processing rules must be explicit, specific and plain;
(3) personal information processing rules must include at least the following:
name and contact information of cyber-data processor;
purposes, means, and types of personal information processing;necessity of processing sensitive personal information and its impact on individuals’ interests;
retention period of personal information and means of disposal after expiry of retention period; and
means and channels through which individuals may access, copy, transfer, correct, supplement, delete, or restrict processing personal information.6.2 Separate consent
The Cyber-data Security Regulation for the first time clarifies that “separate consent” means that specific, unambiguous consents given by individuals for specific processing of their personal information. It is quite vague. Compared with such definition, the draft regulation released in 2021 gives a probably more practical definition of “separate consent”: data processor shall obtain individual’s informed consent for each item of personal information rather than one-off informed consents for multiple items of personal information or multiple processing activities.
6.3 Special requirements on deleting or anonymizing personal information
According to the Cyber-data Security Regulation, a cyber-data processor is obligated to delete or anonymize personal information under the following circumstances:
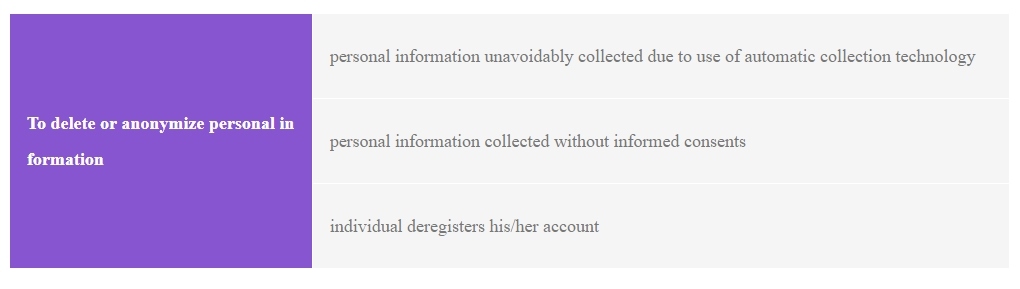
6.4 Detailed conditions of data transfer
If all the conditions listed as follows are satisfied, a cyber-data processor shall provide transmission service to enable other cyber-data processors designated by an individual to access and acquire his/her personal information free of charge (the data processor may charge a reasonable fee if the request for data transfer is clearly excessive):
(1) the requestor’s identify can be verified;
(2) personal information to be transmitted is collected based on the individual’s consent or contracts concluded with the individual;
(3) transmitting personal information is technically feasible; and
(4) transmitting personal information does not harm other individuals’ legitimate interests.
6.5 Regular compliance audit
The Cyber-data Security Regulation requires cyber-data processors to audit their compliance with laws and regulations in respect of processing personal information (NOT DATA) by themselves or through engaging professional security protection audit firms. However, it is not clear that how regular such audit should be. A draft measure released by Cyberspace Administration of China (“CAC”) in August 2023 provides details on how a processor should conduct the compliance audit and how regular such compliance audit should be.
6.6 Special requirements on processing personal information of over ten million people
The Cyber-data Security Regulation requires a cyber-data processor who processes personal information of over ten million people to further comply with regulatory requirements in relation to important data protection (Refer to Section 3).
7. Our Observations
Compared to the draft regulation released in 2021, the Cyber-data Security Regulation has relaxed part of the compliance obligations for cyber-data processors, which will greatly promote the lawful flow and effective use of network data.
The majority of the legal concepts and the data protection mechanism mentioned in the Cyber-data Security Regulation are from and consistent with the Cybersecurity Law, DSL, PIPL and relevant implementation rules. The Cyber-data Security Regulation is to improve and detail the rules of such data protection mechanism.
It is worth noting that the provisions of the Cyber-data Security Regulation are still general and principled. The interpretation and implementation of the provisions of the Cyber-data Security Regulation will need to be clarified, supplemented and improved by the competent authorities in practice.

7F Wheelock Square, 1717 Nanjing West Road, Shanghai 200040, PRC
Zip Code:200040
Phone:+8621 61132988
Fax:61132913
Email:hr@mhplawyer.com